There are two methods you can use for generating a certificate request for Exchange Server 2016:
- The Exchange Admin Center (you can think of this as the GUI method)
- The Exchange Management Shell (or PowerShell, you can think of this as the command line method)
Generating the certificate request (or CSR) using the Exchange Admin Center is generally easier of the two options, and this tutorial will demonstrate how to do it.
To begin, open your web browser and connect to the URL for the Exchange Admin Center on one of your Exchange 2016 servers. After logging in, navigate to servers and then certificates.
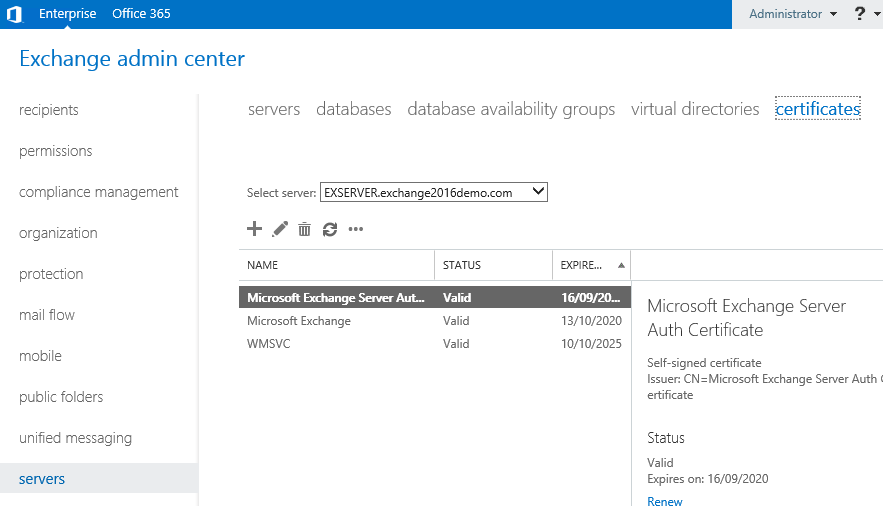
If you have more than one Exchange server in your organization select the correct server from the drop down list, then click the “+” icon to start a new CSR.
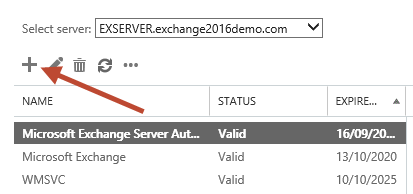
Choose to create a request for a certificate from a certification authority.
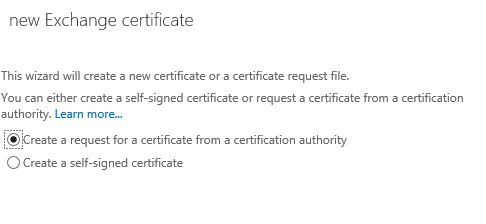
Enter a friendly name for the certificate. You’ll see this name in the list of certificates installed on the server, so make it something that you will easily recognise. For example, there’s already a self-signed certificate named “Microsoft Exchange”, so call your new certificate something different such as “Exchange 2016 SAN Certificate”.
Although wildcard certificates are generally supported for Exchange Server 2016 I am not going to be installing a wildcard certificate in this example.
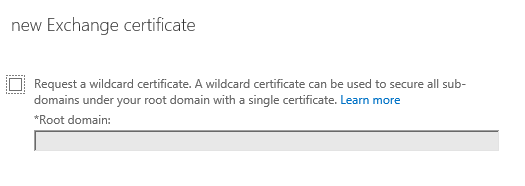
Choose a server to store the certificate request on. The same server is later used to complete the certificate request, and will be the first server that has the certificate installed. You can later export the certificate from this server and import it into other Exchange servers that have the same namespaces configured.
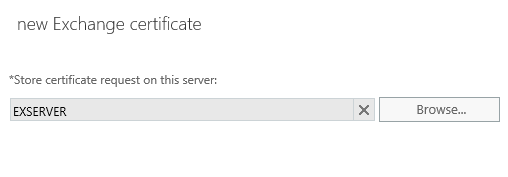
Next we select the domain names to include on the SSL certificate. You’ll notice that the wizard has pre-populated the list based on the namespaces configured on the various Exchange services. However you may also notice if you scroll down that the server’s real name is included in that list due to the default configuration of the POP and IMAP services, even if those services are not enabled. You can edit the entries at this step, but I find it easier to proceed to the next step and modify the list there instead.
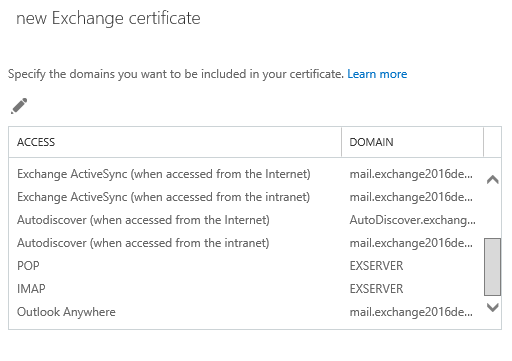
At the next step you can select and remove any unwanted names, edit existing names, or add more names to the certificate request. In this example I’ve modified the list to include only the planned namespaces:
- mail.exchange2016demo.com (for HTTPS services)
- autodiscover.exchange2016demo.com (the Autodiscover CNAME that may be used by non-domain joined devices such as mobile phones)
- exchange2016demo.com (the root domain, which is optional and depends on your specific scenario, but it’s harmless to include it if you’re not sure)
Enter your organization information for the certificate request. This information will form part of the validation process by the certificate authority that is issuing your certificate, so using correct and valid details is important. If any of the details are incorrect the certificate authority may contact you for additional proof of ownership before they’ll issue you a certificate, slowing down the whole process.
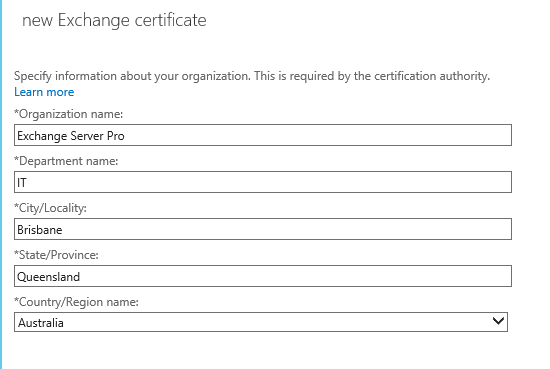
Enter a UNC path to save the certificate request to. The UNC path you provide must be accessible by the Exchange server’s computer account, or by the Exchange Trusted Subsystem group. Simply choosing a UNC path that points to the Exchange server itself should be fine. You’ll also need to be able to access the location yourself to be able to submit the request to the certificate authority.
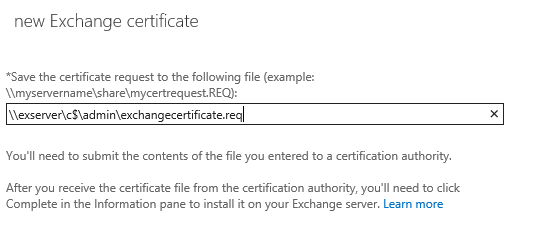
Click Finish, and the certificate request will be generated in the UNC path you chose.
You can now submit the CSR to a certificate authority such as Digicert. When you’ve received your certificate, return to the Exchange Admin Center and complete the pending certificate request.

I searched on net but could not find a sure shot way to create a private key exportable cert request. The GUI doesn’t have any option for it and on shell the command mentioned by MS also fails
$txtrequest = New-ExchangeCertificate -PrivateKeyExportable $True -GenerateRequest -FriendlyName “Contoso.com SAN Cert” -SubjectName “C=US,CN=mail.contoso.com” -DomainName autodiscover.contoso.com,legacy.contoso.com,mail.contoso.net,autodiscover.contoso.net,legacy.contoso.net
[System.IO.File]::WriteAllBytes(‘\\FileServer01\Data\Contoso SAN Cert.req’, [System.Text.Encoding]::Unicode.GetBytes($txtrequest)).
Can anyone advise what I am doing here?
Can I make a request from any domain computer from mmc – certificate?
How would you change the period of validity in the CSR?
Not sure if anybody still gets the error message on the UNC path. Just specify the FQDN of the server in the path.
Hi Paul,
Have just read your article here on requesting a certificate and have previously read your Exchange 2010 version, thank you,
I was not successful in creating an SSL certificate request with our Exch2010 installation so relied on its self created certificate. I have now installed our 1st Exch2016 server which I thought would be successful in this SSL requesting activity. However, it has not been the case. I get an unknown error message every time when following all the steps through.
The folder I am pointing to is empty, the file name is fine and I have changed it many times to elicit another response, Path name used is \\servername\sharename\certreq.req . All to no avail. It fails with:
The Exchange certificate operation has failed with an exception on server exch2016. The error message is unknown error 0xe0434352
No matter what I do I cannot get exchange to create the request. I have searched the internet for the error and cannot find a reference to it. I suspect that the underlying issue may not actually be exchange but at a loss as to where next to look?
I shall be grateful for any pointers you can offer
Did you figure this out? I have the same problem
Thanks
Hi,
Did anyone fix this error. Also get the same for exchange 2013
Thanks
Hi
Just an update as I have managed to get passed this error. It was actually the Mcafee antivirus that was blocking the CSR file from being generated. So check your antivirus or firewall on the server that could be blocking the request. Another thing to do is add the Exchange Trusted subsytem account with full access to the shared folder.
Pingback: Test Lab Guide: Windows Server 2016 with Integrated Exchange 2016, SfB Server 2015 and SharePoint 2016 – A random blog from a sysadmin
Hey, after trying to complete mine still says pending request like it hasn’t worked. Any help would be appreciated.
Hi Paul,
Have just read your article here on requesting a certificate, thank you, it was everything I needed to know. Apart from one thing, what on earth do I do when clicking finish I get the following error?
“error
Please use a valid file name when you run the New-ExchangeCertificate cmdlet on server SERVER with the -RequestFile parameter. The file should not exist in target folder. Parameter name: RequestFile”
No matter what I do I cannot get exchange to create the request.
The folder I am pointing to is empty, the filename is fine and I have changed it many times to elicit another response, all to no avail.
I have searched the internet for the error and cannot fond a reference to it, hence I thought you may have some insight.
Thank you in advance if you do..
Best regards
Mike
The Real Person!
Author Paul Cunningham acts as a real person and passed all tests against spambots. Anti-Spam by CleanTalk.
What path and filename are you trying to use?
\\lab-dc01\C:\Users\Administrator\Desktop\certreq.txt is what works for me on a just created certificate.
Dear amit ,Your path and file name is wrong ,kindly follow the below steps
1)Create a one folder in C drive(certrequest) and share that folder with full access
2)Put path \\lab-dc01\certrequest\certreq.req
Instead of C: i’d use C$
I had the same issue as I was using remote server UNC path to save Cert.req file. It got fixed, after I have created local shared folder on exchange server and saved the request locally.
try that.
neither C$ nor C: worked for me when trying to save .req file on remote unc path.
Hi Paul, I have a split DNS, local AD is iscksa.net and my external domain is iscksa.com. When I generated my CSR, I remove the iscksa.net entries. I completed the installation. OWA works fine, but when I tried to setup Outlook, I was prompted to login as @iscksa.net. Is it because I remove the iscksa.net in the certificate and I am being logged in to my AD which is iscksa.net?
The Real Person!
Author Paul Cunningham acts as a real person and passed all tests against spambots. Anti-Spam by CleanTalk.
The certificate is for securing your HTTPS connection between client and server. It has nothing to do with the domain name of the user who is logging in.
I have a SAN certificate. I got it bound to smtp and iis, I don’t require pop or imap or uc or exchange uc.
What if I delete the three certificates what exchange had generated after installation?
What’s the impact of it.
Hi Paul,
Is SAN certificate still recommended and prefered over a wildcard certificate?
I asume wildcard certificate in Exchange 2016 requires additional configuration for IMAP and POP3 on SSL (set-imapsettings and set-popsettings) ?
And does CertPrincipalName be set for Outlook-Provider in Exchange 2016 with wildcard?